Blockchain Byte - Week 20 : Transaction Validation

Table of Contents
- Recap
- Transaction Validation
- Nodes
- Mempool
- Public Key Verification
Recap
To recap, last week we introduced at a high level how crypto payments or funds transfer is initiated and how "value" moves across transactions in a blockchain.
We explained
- Transaction Outputs
- Transaction Inputs
- UTXO (Unspent Transaction Outputs)
and how transactions are signed by wallets with digital signatures which "links" the wallets to transactions in the blockchain.
So, there are three parts to "ownership" of crypto currency -
A. Addresses - Whose funds are these?
B. Digital Signatures - Are these my transactions?
C. Keys (Public & Private) - Password and account details
Once we have established that the funds are ours & all the required checks are passed, next step is for the transaction to be validated. What does it mean? Let us explore
Transaction Validation
So, Sender has initiated the transaction to transfer 10 BTC to Beneficiary. What happens next? The transaction needs to be verified or validated. It's the first step of a two step process -
Step 1 - Verification / Validation
Step 2 - Authorization
In traditional banking, the verification function is carried out by a bank staff or system who or which verifies the relevant fields like name, signature, amount etc. They also check whether the customer has enough funds in his / her account to carry out the transaction.
In crypto world, there is no bank staff or centralized authority who can carry out this function. Instead, the validation function is carried out by nodes. What is a node?
We explained that a blockchain (like Bitcoin blockchain) is a peer-to-peer network with a network of nodes connected to each other and is decentralized meaning none of the nodes serve as a central server where all the transaction processing is centralized. Let us recap our explanation on nodes from Week 11.
Nodes

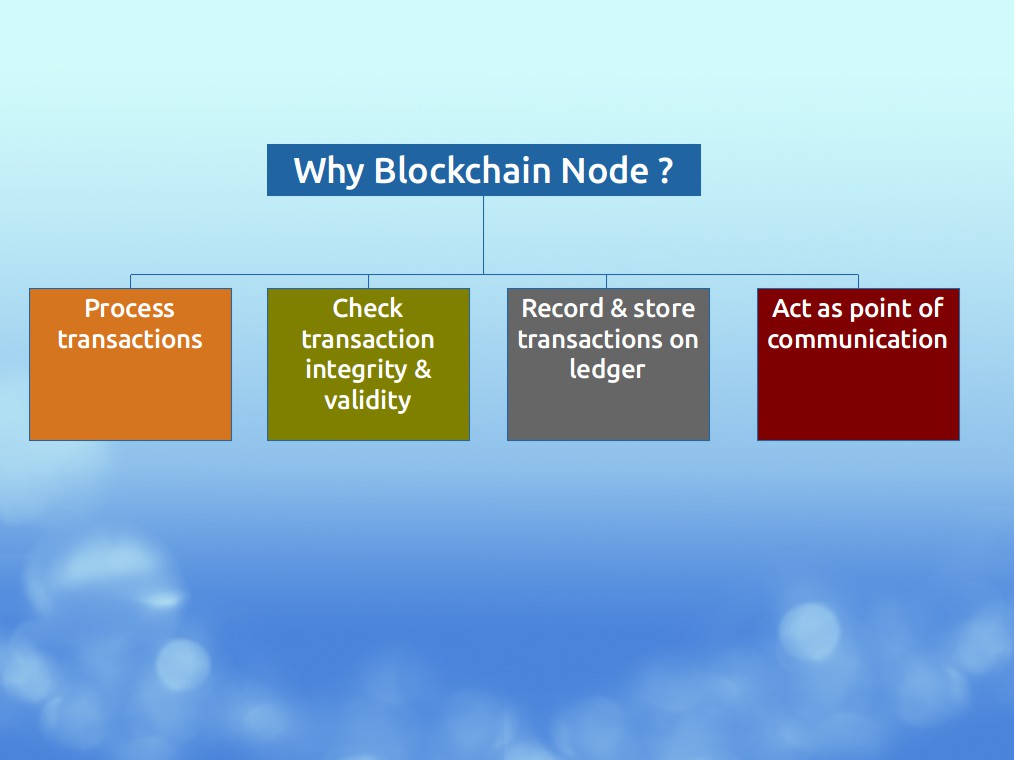
The main goal of a node is to provide reliable data storage in the blockchain network.
There are different types of nodes depending on the roles they are assigned within the blockchain network. You can compare it to different roles in a back office where each person has an assigned role in line with his or her responsibilites. One of the roles is to check transaction integrity & validity.

At a high level, when a transaction is initiated, the processing nodes within the blockchain
A. take these transactions
B. check their integrity &
C. record them on the ledger
In addition to the above, they are also a point of communication in the blockchain network which is called the network routing function.
The below diagram summarizes it clearly :
The transactions are initially propagated to all the nodes forming part of the network so that all the nodes can "see" the transaction. The nodes then go about verifying the transactions. How? For that, we need to first dive into something called MEMPOOL.

Mempool
As transactions get propagated to all the nodes, it forms part of a pool of transactions which are unverified or unconfirmed. Just like transactions in traditional banking goes through two stages -
- Verification stage - Transactions are input into the system & verified but not yet confirmed since they need to be rechecked before being part of the bank's ledger
- Authorization stage - The verified transactions are
- Confirmed or authorized and
- Added to of the bank's ledger after being double checked by a competent supervisor.
Visualizing the above :
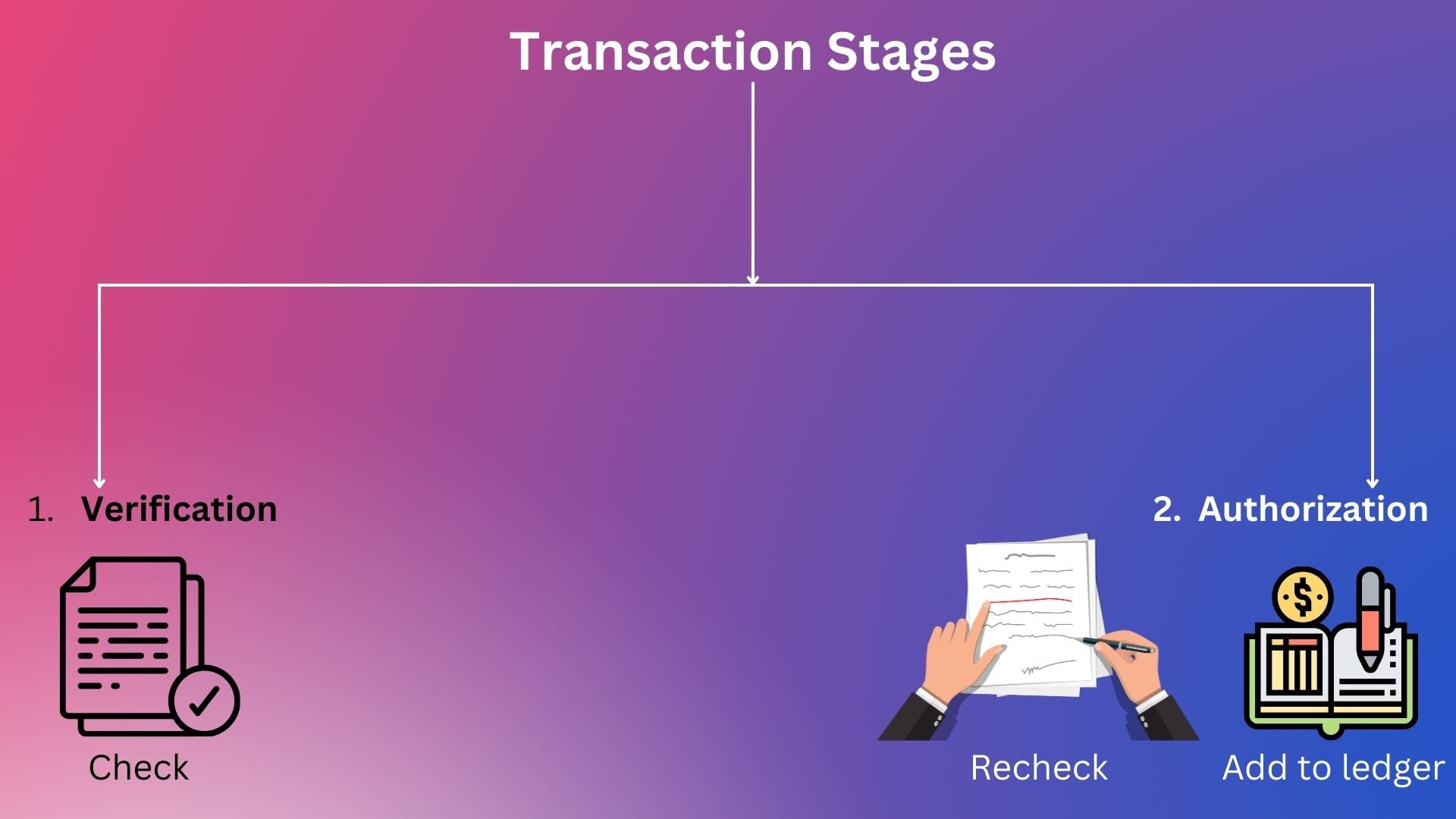
Similarly, a transaction in a blockchain first forms part of a pool of unverified or unconfirmed transactions called MEMPOOL (short for memory pool).
Beneficiary's wallet will be able to track any incoming payments that has been initiated in the network but not yet confirmed from this mempool.
Public Key Verification
Now, how does a node verify the integrity of these transactions without physically being able to verify the transaction like a bank staff or without physical access to any documentation of the transaction?
This is where the second algorithm of digital signature comes into play which is :
A SIGNATURE VERIFYING ALGORITHM, that allows anyone to verify a signature, given the message and the public key (corresponding to the private key used in the signing algorithm).
We know that a public key is generated from the private key and address is generated from a public key. Also, reverse engineering one from the other is not possible due to usage of highly complex mathematical formulas which works only one way.
But anyone with the public key can verify that the transaction has been signed from its paired private key.
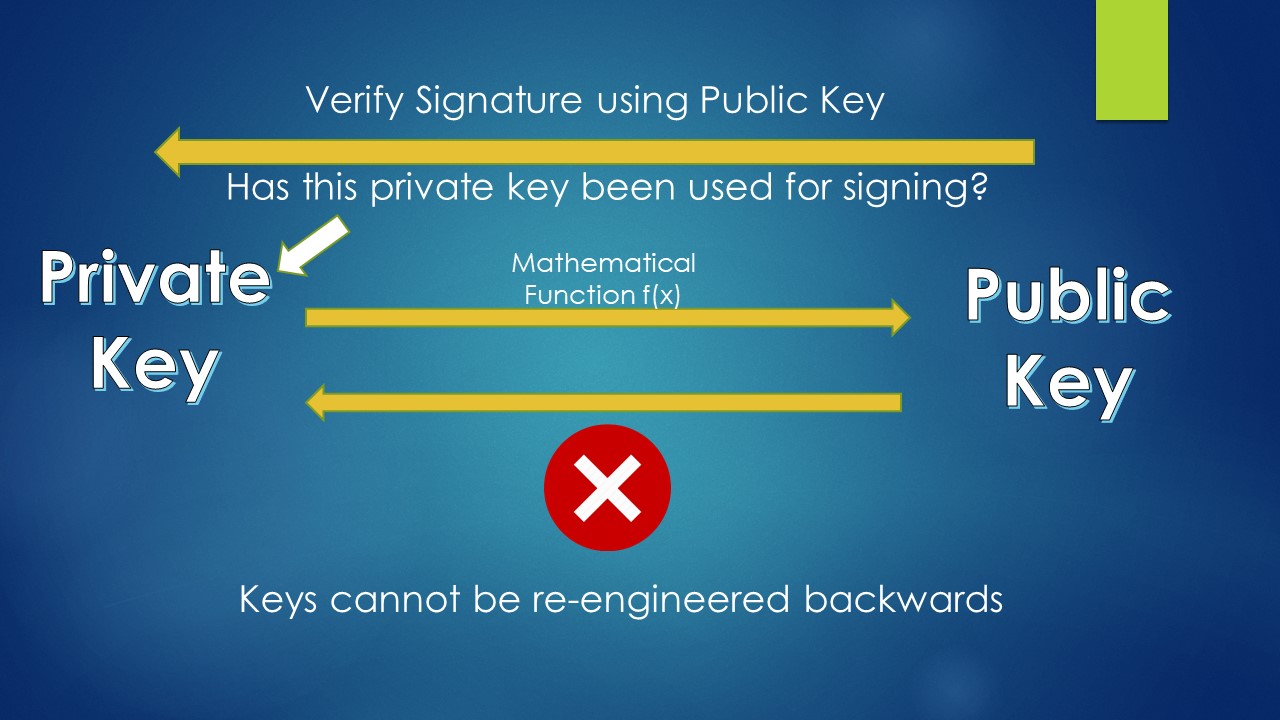
The signature verifying algorithm allows a node to verify the signature using the public key. The logic is that a signature can only be produced by someone with access to a private key & anyone with access to the paired public key can use the algorithm to verify the signature.
So, only a public key which is the pair to its private key can verify the authenticity of the signature.
This confirms ownership of the signature since the public key is generated only from the private key used in signing the transaction.
Now, let us summarize with the transaction sequence below:
- Sender wants to send 10 BTC to Beneficiary
- IDENTIFY UTXO - Sender's wallet searches for Sender's UTXO(s) tied to that wallet for funds which can be "spent" or "extinguished"
- GENERATE TXN INPUT - After identifying the relevant UTXO(s) for source of funds, a transaction input is generated which extinguishes or reduces the UTXO
- SIGN TXN - The transaction is signed by the Sender's wallet
- CHECK TXN - The transaction input contains a locking & unlocking script which are run to ensure that all the conditions regarding amount, beneficiary address etc are satisfied before transfer of value
- PROPAGATE TXN - The transaction is propagated to all the nodes in the network.
- MEMPOOL - The transaction forms part of the mempool (pool of unverified transactions)
- VALIDATE TXN - Using digital signature, the nodes validate the transaction using the transaction details and the public key.
Now, if everything related to the transaction is fine, how does it get authorized meaning how does it get added to the ledger and become an immutable record?