Blockchain Byte - Week 28 Blockchain Protocols
Recap
Last week we explained "The Byzantine General's Problem" which is used as an analogy to describe the challenge of establishing consensus in a decentralized network where some nodes can be dishonest or nodes are connected using an insecure network.
We also discussed the below solutions to the Byzantine General's problem.
1. Hashing
Hashing is the process of having an input of any length, running it through a hashing algorithm and getting an output of fixed length. This means the hash output generated is independent of the length of the input.
2. Proof of Work
A mining node can add blocks to a blockchain only after solving hard cryptographic puzzles. And these nodes compete with each other to add blocks to the blockchain. The puzzle is so difficult to solve that there are specialized hardware only to solve these puzzles. The cost factor to mine a block is the processing power and electricity expended for solving this problem.
The solution to the cryptographic problem is called PROOF OF WORK.
Both the above make the network Byzantine Fault Tolerant (BFT). It is a feature of reaching an agreement or consensus regarding transactions & blocks based on Proof-of-work, despite some nodes not responding or responding with malicious messages.
The main objective of BFT is to safeguard the Blockchain network even in the presence of faulty nodes.
This week let us understand Blockchain Protocols.
Blockchain Protocol
Let us take a moment to go through the below visualization which depicts the flow of a typical transaction in traditional banking system:
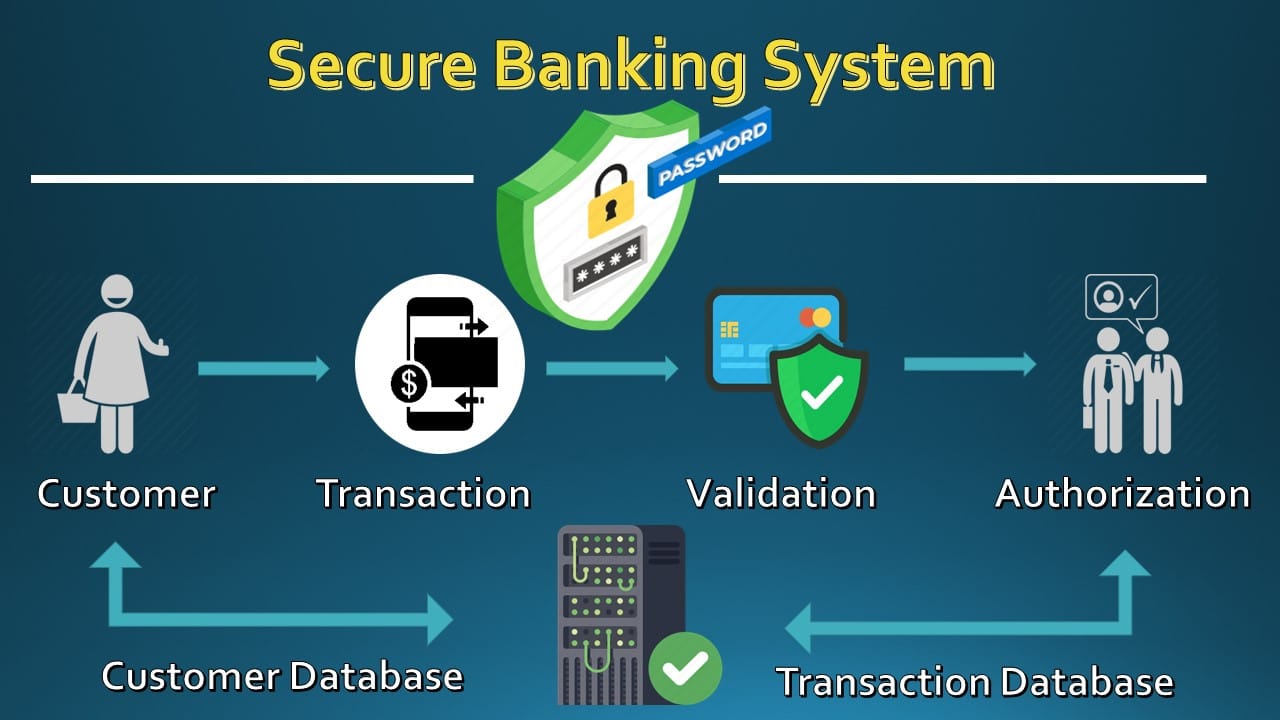
- Customer logs into the banking system.
- System checks the customer login & password with that in the customer database
- Customer initiates transaction
- Transaction is checked and validated (Does the customer have required funds? Is he or she authorized to do such transactions? etc)
- Transaction is authorized
- Transaction forms part of transaction database
There are control mechanisms at various stages as :
- There is a secure banking system which the customer has access to once the bank onboards a customer.
- The system validates the customer login and password
- The transaction is checked for validity & accuracy by the system or a banking staff
- The transaction is again checked before authorization either by the system itself (through customer 2FA or authorization password) or by another senior staff.
So, basically there is an infrastructure &/or rules around which transactions are done in traditional banking in line with the below framework :
- Central Bank rules & regulations
- International laws
- Internal Policies & Procedures of the individual banks
All of the above processes, infrastructure, framework & rules (and maybe more as Financial Services is one of the most regulated sectors) are the protocols around which traditional banking functions & thrives.
Another example of protocols that we use are Internet protocols like TCP / IP, HTTPS etc related to how data packets are transmitted efficiently over the information highway known as the Internet.
Now, let us take a moment to visualize a blockchain :
At a very high level, the major infrastructure in a blockchain is nodes & protocols. (It is not that simple but for now, this will suffice!!) .
At it's core, a Blockchain protocol is a set of rules & algorithms that govern the behavior of a blockchain network. It provides a framework for participants to interact with one another & maintain consensus, ensuring the integrity & security of the system.
In simpler terms, it serves as the backbone of a Blockchain network, enabling the decentralized & transparent nature of the technology. (Source : here)
For example, the Bitcoin white paper laid out a set of computing rules for the distributed database. The Bitcoin protocol includes algorithms that regulate the mining function across the network. The difficulty of the Proof of Work algorithm is adjusted dynamically by the protocol. The protocol also halves the rate at which new bitcoins are created every 4 years.
Protocols ensure :
- Decentralization as the nodes will behave as per the underlying protocols of the network without any central entity fixing the rules as per their whims & fancies.
- Adequate checks and balances against double spending.
- Security on the Blockchain
Examples of some major protocols are:
- Bitcoin: Bitcoin’s protocol serves as the foundation for the world’s first cryptocurrency, enabling peer-to-peer digital transactions using Proof of Work.
- Ethereum: Ethereum’s protocol allows for the creation of decentralized applications (DApps) and smart contracts using Proof of Stake.
- Ripple: Ripple’s protocol focuses on facilitating fast and low-cost cross-border payments for financial institutions. Ripple uses the Ripple Protocol Consensus Algorithm (RPCA) & it's native cryptocurrency is the XRP.
- Hyperledger Fabric: Hyperledger Fabric is used for enterprise blockchain solutions, especially in supply chain and healthcare applications. It aims to develop enterprise-grade Blockchain protocols & frameworks for different industries.
- Cardano : Cardano’s protocol emphasizes sustainability, scalability, and interoperability for blockchain networks. It employs a unique proof-of-stake consensus mechanism called "Ouroboros".
- Polkadot : Polkadot’s protocol enables the interoperability of multiple blockchains.
- Chainlink : Chainlink's protocol connects smart contracts to real-world data sources, enhancing their functionality.