Blockchain Byte - Week 32 Blockchain Layers

Table of Contents
- Recap
- Layers in a Computer
- Blockchain Layers
Recap
During Week 32, we explained blockchain specific attacks like :
- Sybil Attacks &
- 51% or Majority attacks
A Sybil Attack is a type of attack on a computer network service in which an attacker subverts the service's reputation system by creating a large number of pseudonymous identities and uses them to gain a disproportionately large influence.
A Blockchain is said to be under 51% attack when an attacker operating on a Blockchain network has successfully gained control of over half of the nodes operating in the network.
A Sybil attack is also often used to create a 51% attack in most situations. They both work unanimously. The attack first starts with the creation of one or more fake nodes and then these fake nodes move to dominate the entire network, where fake nodes outnumber the honest nodes.
This week, let us explore the Blockchain Layers!!
Layers in a Computer

Before we get into Blockchain layers, let us analyze something we are familiar with - our laptop or computer. We use it everyday at work and home. Things happen under the hood from the time you switch on your computer or laptop. What happens under the hood? Let us see
- Our laptop or computers consist of switches, circuits, boards, disks etc. This is what we call Hardware.
- Once the computer starts up, there is something called BIOS (Basic Input-Output system which is used to start the computer system after it is powered on. The BIOS also manages the data flow between the computer's operating system (which we will discuss in a bit!!) & the attached devices like hard disk, keyboard, mouse etc. (You can read more about BIOS here)
- What is an operating system? We all heard about Windows operating system, Mac OS & Linux for desktops or laptops, IOS or Android for mobiles & tablets .
As per Wikipedia,
An operating system (OS) is SYSTEM SOFTWARE that manages COMPUTER HARDWARE, SOFTWARE RESOURCES, & provides common services for computer programs.
That means if we open multiple applications (Say, word and excel) together, it is the operating system which ensures optimal utilization of computer resources so that both the programs can perform efficiently when they are open together. If we try to open like 50 excel files, we can see that the computer becomes slow or maybe "hangs". This is because the operating system cannot allocate the necessary computer resources to run that much files.
- The next is Application Software which is defined (as per wikipedia) as :
An application program or software is a computer program designed to carry out a specific task other than the one relating to operating the computer itself, typically to be used by end users
Some examples of Application Software are Microsoft Word used for word processing or Microsoft Excel for spreadsheets etc.
Visualizing the above layers from bottom to top :

Now, with that understanding, let us explore the layers in a Blockchain.
Blockchain Layers
We know that Blockchain is a decentralized network of nodes. So, how can it have layers? A Blockchain is like one large system consisting of multiple computers, laptops or mobiles connected to each other as nodes run by shared & underlying consensus & security protocols. A good example of this is Ethereum Virtual Machine or EVM (We will discuss about EVM or Ethereum Virtual Machine at a later stage!!)
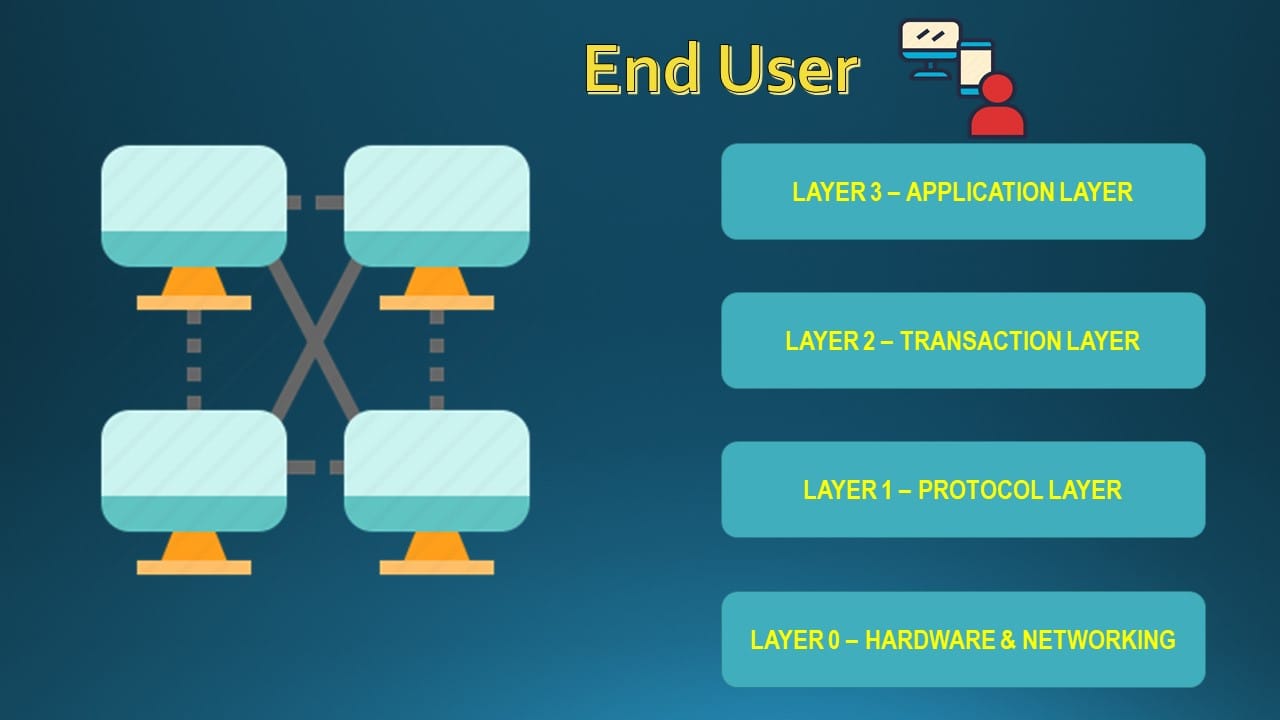
The layers in a Blockchain are as below with Layer 0 at the bottom & Layer 3 at the top:
- Layer 0 - Hardware & Networking
- Layer 1 - Protocol Layer (consensus, mining, security, decentralization)
- Layer 2 - Scaling Solutions (Blocks, transactions etc)
- Layer 3 - Application Layer (Decentralized Apps, DAOs etc)
Let us explore each of them.
Layer 0 - Hardware & Networking
Blockchains are constructed using P2P (Peer-to-Peer) network architecture which means in simple terms - multiple computers connected to each other to form a network mesh where data or information can be shared & value transferred within the network.
Also, the nodes "communicate" with each other to propagate transactions, validate transactions and come to an agreement on the legitimacy of the transaction. This communication is made possible through Layer 0 networking.
Examples of Layer 0 Blockchains include Polkadot, Avalanche, Cardano etc.
Layer 1 - Protocol Layer
This is the most important layer in a Blockchain where the basis of "agreements" for nodes to validate & agree on transaction validity & legitimacy is coded. This ultimately results in transaction authentication. In other words, the consensus, proof-of-work protocols etc exist in this layer. Without this layer, no validation or authentication can happen.
Bitcoin, Ethereum, Solana, Cardano, Ripple etc are examples of Layer 1 Blockchains.
Layer 2 - Scaling Solutions
Layer 1 blockchains establish the base functionality, security, and decentralization. But the issues around scalability and efficiency when passing transactions gave rise to layer 2 solutions as there are limitations on the quantum of transactions that can be passed at a particular point in time in Layer 1 Blockchains.
Layer 2 refers to secondary frameworks that run on top of layer 1 network to facilitate faster and cheaper transactions while inheriting the security at the base-layer.
E.g., Lightning Network for Bitcoin enables fast off-chain transactions.
Layer 3 - Application Layer
The Application layer is what the end user sees when trying to access a Blockchain. This layer consists of programs that end-users use like Decentralized Applications (also called DApps), User Interfaces (UIs), Smart Contracts etc.
It is the layer 3 or Application Layer which links Blockchains to the end users & gives rise to use cases. We can think of the IOS or Android ecosystem where it is the apps in those phones which connects the end user to the underlying architecture within the Iphone or the Android phone and creates value to the end user.
E.g., wallets like Metamask, NFT platforms like Opensea, DeFi apps like Uniswap
Visualizing the above layers :